
In the ever-shifting realm of mobile technology, the security paradigms of Android and iOS unfold as a compelling narrative of contrast and similarity. Android, with its roots in open-source philosophy, presents a vast spectrum of customization and choice, catering to diverse user needs. This openness, however, gives rise to a varied ecosystem where devices and versions each bear their unique security footprint, leading to a patchwork of protection standards.
Conversely, iOS operates within a meticulously curated environment, its closed ecosystem synonymous with controlled uniformity. This approach typically yields more consistent security updates and a fortified stance against malware, albeit at the expense of limited customization for the end-user.
Both Android and iOS have evolved an array of security mechanisms aimed at shielding users, encompassing app permissions, encryption methodologies, secure boot sequences, and a regimen of updates. Yet, the real-world efficacy of these security measures is often as much a function of user behavior as it is of technical design. Practices such as downloading from unverified sources, weak password usage, and overlooking updates can significantly undermine the security posture of a device.
The domain of mobile security is not merely a technical arena but a dynamic ecosystem where user awareness and behavior significantly influence security outcomes. As we navigate the intricacies of Android and iOS security, it’s imperative to acknowledge that the sanctity of our digital existence is often a reflection of our choices and habits.
(more…)



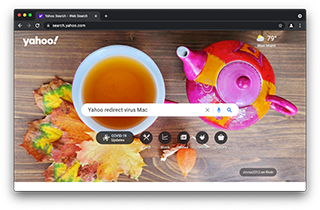 It has been years since Yahoo became a piece of cybercriminals’ traffic monetization puzzle, but this is still a scheme whose gist seems murky.
It has been years since Yahoo became a piece of cybercriminals’ traffic monetization puzzle, but this is still a scheme whose gist seems murky.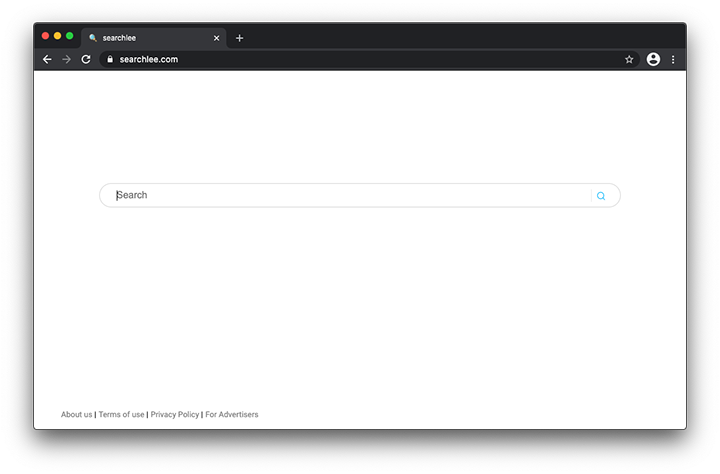 In a recent move, an ill-famed Mac malware gang has unleashed a new browser hijacker that constantly forces hits to searchlee.com.
In a recent move, an ill-famed Mac malware gang has unleashed a new browser hijacker that constantly forces hits to searchlee.com. Android users are on the receiving end of a virus campaign that promotes the Taicheetee.com site by spawning incredibly annoying pop-ups and browser tabs.
Android users are on the receiving end of a virus campaign that promotes the Taicheetee.com site by spawning incredibly annoying pop-ups and browser tabs. This move fits the mold of the ongoing trend of pressuring victims into submitting a ransom. As before, this harmful code is being served via TrickBot, a modular banking Trojan that exhibits malware loading properties. It used to be that the Trojan would deploy the Ryuk ransomware as the final-stage payload.
This move fits the mold of the ongoing trend of pressuring victims into submitting a ransom. As before, this harmful code is being served via TrickBot, a modular banking Trojan that exhibits malware loading properties. It used to be that the Trojan would deploy the Ryuk ransomware as the final-stage payload. Have you been thinking about starting an online business? Maybe you want an extra source of income or more freedom and flexibility with your time. Creating a successful online business from scratch is inexpensive and you can do it regardless of your educational or professional background. Don’t waste more time focusing on what could fail, for you have an opportunity to make unlimited income with a well-crafted online business.
Have you been thinking about starting an online business? Maybe you want an extra source of income or more freedom and flexibility with your time. Creating a successful online business from scratch is inexpensive and you can do it regardless of your educational or professional background. Don’t waste more time focusing on what could fail, for you have an opportunity to make unlimited income with a well-crafted online business. The two arrests happened in the beginning of June just several days after infosec specialists from Tencent and Qihoo 360 had discovered initial virus attacks.
The two arrests happened in the beginning of June just several days after infosec specialists from Tencent and Qihoo 360 had discovered initial virus attacks.