
Cyber analysts from CloudSEK have reported an investigation into malicious attacks, revealing that hackers have started utilizing a Java-based Trojan called DogeRAT for Android. The creators of this malware are offering a wide array of malicious functions to clients for just $30 per month.
DogeRAT is an exceptionally effective virus that grants the operator covert control over the victim’s Android device. It stealthily steals sensitive information, including contacts, SMS messages, and online banking credentials. Moreover, the Trojan can perform unauthorized transactions, send spam messages, manipulate infected files, and even exploit the device’s camera to take photos without the user’s awareness. Within the hacking community, DogeRAT is being promoted as a service and has gained considerable popularity.
The true danger lies in the Trojan’s ability to disguise itself. It assumes the shape of both popular legitimate applications and fake ones, often impersonating gaming or banking apps. The researchers have identified approximately a thousand counterfeit applications associated with DogeRAT. Particularly notable among these disguises are replicas of well-known products such as the Opera Mini browser, a non-existent Android VulnScan OS, a clone of the ChatGPT bot, and premium versions of YouTube and Netflix.
Following the common pattern observed in many malware campaigns operating under the Malware-as-a-Service (MaaS) model, DogeRAT is being promoted by its developer through a Telegram channel. Initially, a limited-functionality version of DogeRAT was made available for free on GitHub, primarily as a demonstration of its capabilities. However, for just $30 per month, clients can avail themselves of an extensive array of features, such as screenshot capture, image theft, retrieving clipboard content, and logging keystrokes.
In the Readme.md file available in the code repository, the author of the Trojan emphasizes that he or she doesn’t endorse any shady or otherwise unethical use of this application, and the responsibility for potential abuse is entirely on the user.
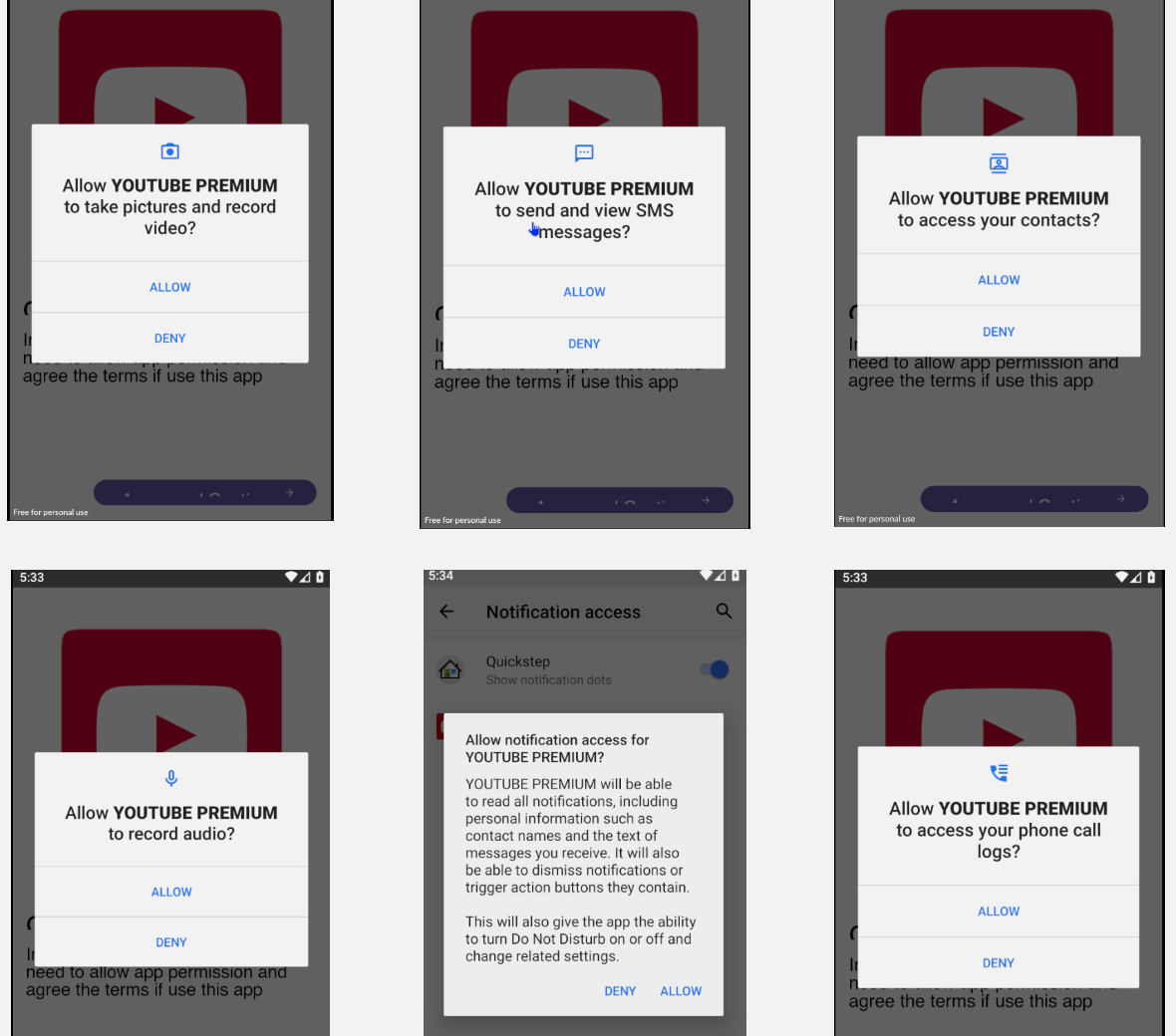
Once installed on a target device, this Java-based malware, camouflaged as a popular legitimate application, seeks the necessary permissions to collect data. Subsequently, the collected data is discreetly uploaded from the compromised device using Telegram as the communication channel, successfully evading detection and exfiltrating sensitive information behind the victim’s back.

