Conti ransomware, a spinoff and likely heir of the infamous Ryuk, has recently launched a data dump website to take its extortion tactic to the next level.
 This move fits the mold of the ongoing trend of pressuring victims into submitting a ransom. As before, this harmful code is being served via TrickBot, a modular banking Trojan that exhibits malware loading properties. It used to be that the Trojan would deploy the Ryuk ransomware as the final-stage payload.
This move fits the mold of the ongoing trend of pressuring victims into submitting a ransom. As before, this harmful code is being served via TrickBot, a modular banking Trojan that exhibits malware loading properties. It used to be that the Trojan would deploy the Ryuk ransomware as the final-stage payload.
According to security researchers, Ryuk isn’t being promoted this way since July 2020. Instead, criminals associated with the TrickBot malware distribution network switched to pushing the Conti ransomware.
Conti is a new Ransomware-as-a-Service (RaaS) platform with limited cybercriminal audiences. It has hired seasoned crooks to spread the file-encrypting threat. The operators get their cut from ransom payments and give the rest to ne’er-do-wells who execute a successful extortion attack.
As per statistics derived from the ransomware identification service “ID Ransomware”, Conti infections have been steadily growing since mid-June 2020. Meanwhile, the propagation of Ryuk has taken a nosedive ever since. The overlapping of these two opposite trends proves the theory that the Ryuk group is now plaguing enterprise networks with the Conti ransomware.
Conti attackers set up a site for data leaks
Since last November, some ransomware crews that target organizations have been exfiltrating data before scrambling it with cryptographic algorithms. These files are abused to put an extra burden on the victim as the felons threaten to spill them if the business turns out to be reluctant to pay the ransom for data recovery.
The Conti ransomware has been in the wild for only a few months now, but its data dump site named “Conti.News” was set up in late August. Its contents include records relating to more than 20 affected companies, some of which are large and reputable businesses. The site has a separate page for every contaminated organization, where small portions of the pilfered data are published as a way to pressure the victim.
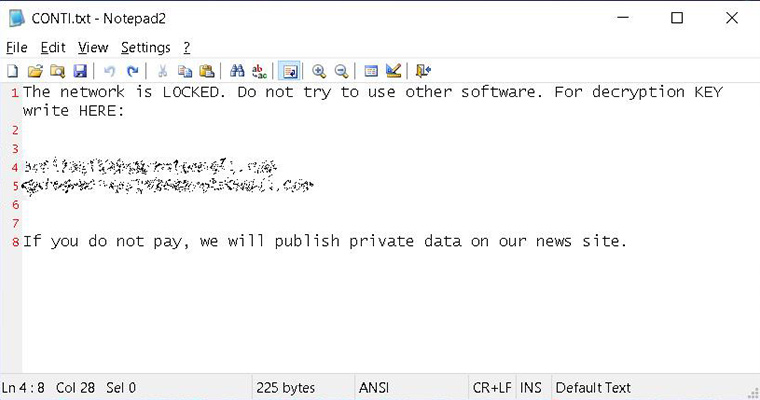
The new ransom notes dropped by Conti now also include a phrase that the adversaries will publish files on their news site unless the ransom is sent within a specified deadline. Overall, leaking data in addition to encryption is a disgusting tendency in the ransomware environment. It means that the incident cannot be addressed even if important files are backed up.
Tags: conti, cyber attack, data leak, RaaS, ransomware

